
Why open-source software security is more important than ever

Open-source software is a key component in modern applications. It has created a new era in software development, promoting a free exchange of ideas in the developer community and enabling developers to build more functional software, faster. Based on most estimates, 70-90% of any modern software includes open source code.
At companies where developers use open source, innovation is constant and iterations are short. But any third-party code (including open-source packages) can introduce security risks. And the more widely used any open-source package is, the bigger the security vulnerability impact can be. Developers and companies using open-source need to truly understand — and know how to mitigate — the risks that come with those packages and libraries.
In May 2022, Snyk and the Linux Foundation collaborated to research the current state of the open-source ecosystem. The research focused on how developers detect and address risk, and on how organizations need to adapt to automate and improve the testing of open-source components. From this research, Snyk and the Linux Foundation developed the State of Open Source Security Report 2022.
The report details significant security risks resulting from the widespread use of open-source software within modern application development, as well as how many organizations are currently ill-prepared to effectively manage these risks. Specifically, the report found that:
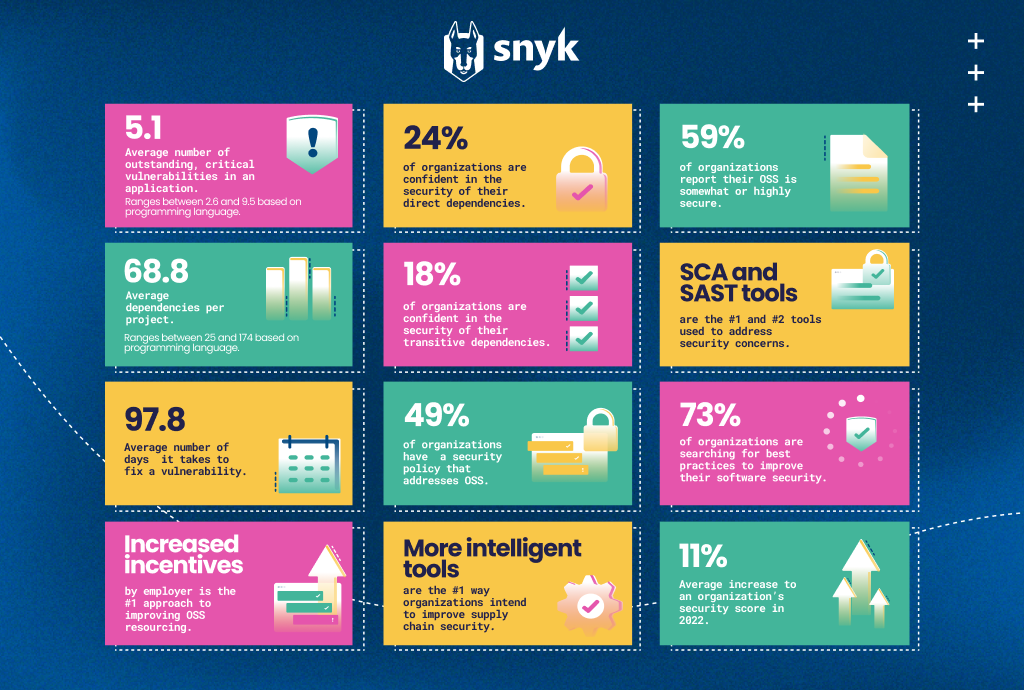
- Four out of every ten (41%) organizations don’t have high confidence in their open-source software security.
- The average application development project has 49 vulnerabilities and nearly 80 direct dependencies.
- The time it takes to fix vulnerabilities in open-source projects has steadily increased, more than doubling from 49 days in 2018 to 110 days in 2021.
What are the big risks in open source, and how can companies manage those risks?
1. Understand that dependencies bring complexity
The average project has 49 vulnerabilities spanning 79 direct dependencies.
Open-source security becomes a bigger challenge as the software supply chain becomes more complex. The software supply chain is an attractive entry point for malicious actors, because they can take advantage of vulnerabilities in small, but widely used libraries. Remember Log4Shell? It made incoming logged data vulnerable to RCE (remote code execution) attacks. It was a critical weakness inside of a popular open source logging framework — a vulnerability inside of a dependency.
Only 24% of organizations are confident in the security of their direct dependencies. And while a third (37%) of organizations report that dependencies are easy to track, these dependencies are not necessarily in a secure state.
2. Lay the groundwork with security policies
Only 49% of organizations have a security policy that explicitly addresses the development and use of open-source packages. This is understandable in smaller organizations, where resources are limited. But research also showed that 27% of medium-to large companies don’t have an established security policy in place. When you consider how much data each of these companies might be processing, 27% is an alarming statistic.
Of the people surveyed at organizations that don’t have an open-source security policy, 30% readily recognize that no-one on their team is responsible for addressing open-source security. On a positive note, this means that 70% of those surveyed could identify someone at their organization who is working on it, even though they don’t have clearly defined policies for it. This might suggest that even at organizations without a top-down security policy, someone is working as a security champion.
3. Use the right tools and strategies
Nearly three-quarters (73%) of organizations are searching for best practices to improve their software security. But what does this mean?
As noted above, prioritizing a security policy (and ownership of that policy) is fundamental. Beyond that, organizations need to invest in a diverse set of tools to help them build more secure applications. In addition to SCA (software composition analysis) tools, organizations’ preferences regarding security testing vary. SAST (static application security testing) tools are used at 35% of organizations, IaC (infrastructure as code) is used at 35% of organizations, and web application scanners at 32% of organizations. Each of these solutions provide unique security benefits.
Over half of respondents expressed interest in obtaining training and certifications for secure software development. This suggests a growing interest in learning to build reliable open-source security practices. It also extends to an interest in encouraging developers to learn best practices and acquire accreditation. Fortunately, many resources are available to train development teams on how to think about and enforce good open-source security practices.
Certification programs are also widely available. For example, the OpenSSF’s course on developing secure software provides both a training course and certification of completion. (The OpenSSF is part of the Linux Foundation.) Snyk also provides a full library of free security education information, designed for developers.
The future of open-source security: policy, tools, best practices
Using open source packages safely requires a new way of thinking about development security that many organizations have not yet adopted.
Every organization needs to have a CISO, a person or team tasked with key security responsibilities. When key CISO capabilities are present and available, an open-source security policy will follow. Actionable policies must be put in place and socialized across teams — starting with CISOs and developers, and moving throughout the organization.
The software security tools market extends from source code management through to the entire development lifecycle. Organizations on average use 2.8 security tool categories, and SCA and SAST are the leading tools used to address open-source security. Software security must be managed across each step, and accomplishing all with just two or three tools isn’t feasible. Organizations should take a closer look at additional security tools and determine where they can add the most value.
73% of organizations said understanding best practices for secure software development was a leading way to improve the security of the open-source software supply chain. A key reason for the wide interest in best practices is that building secure software involves the entire development lifecycle. At each step in the process – from source code management, build services, and packaging to software delivery and deployment – there are numerous best practices to be followed. Organizations that want to strengthen their future security posture should take advantage of the many courses and certification programs on best practices that are available.
Learn how organizations manage open source risk in this report from Snyk and The Linux Foundation.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network
