
Security agencies warn public to not download Pink WhatsApp. (Image source – Shutterstock)
Everything you should know about Pink WhatsApp
The Pink WhatsApp scam has been affecting individuals and organizations all over the world. In Asia, victims of the scam have grown with governments warning the public not to download the malicious app.
In India, the police have released advisories warning the public to be vigilant of the Pink WhatsApp scam while similar advise has been issued in Malaysia. Spreading through forwarded messages on WhatsApp as a new version of the chat app, the message links users to download the app and then proceeds to steal credentials.
The scam was first uncovered by internet security researcher Rajshekhar Rajaharia in April 2021. While it’s been more than two years, the messages are back again, and the number of victims is growing.
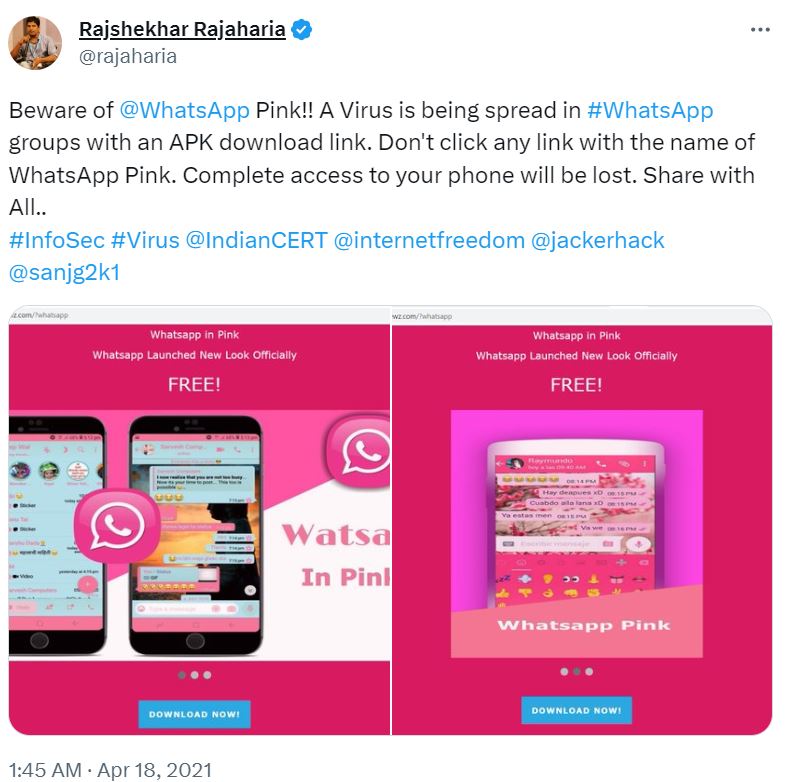
A Tweet exposing Pink WhatsApp when it first started in 2021.
To understand more about Pink WhatsApp and how users can better secure their mobile devices, Tech Wire Asia speaks to Jan Sysmans, Mobile App Security Evangelist at Appdome.
What is Pink WhatsApp?

Jan Sysmans, Mobile App Security Evangelist
According to Sysmans, For Pink WhatsApp, users are sent a link to download an app claiming to be an official update that improves WhatsApp’s functions such as the selection of photos, length of videos and size of documents. The app is in the Android Package Kit (APK) format. APKs are installation files for Android apps. They can be downloaded directly from the Internet as well as third-party app stores, instead of the Google Play Store.
“Most malware and malicious apps follow a similar distribution model as Pink WhatsApp. Hackers, fraudsters and other malicious entities will typically create fakes, clones or pirated copies of popular apps and games that are infected with malware. These apps can be installed via non-official app stores or direct links. Such apps are commonly referred to as Trojan Apps or Trojans,” explained Sysmans.
Regarding Pink WhatsApp, Sysmans pointed out that the malware masquerading as a legitimate WhatsApp update can steal banking details, one-time passwords (OTPs), photos and contacts once it is downloaded onto a device. Victims are often tricked into downloading the application through social media or a phishing message with a download link.
The victims
There have been several cases of fake app scams:
In May, there were attempts to scam Malaysians with a fake Bank Negara application. Victims received messages, purportedly from Bank Negara, the country’s central bank, informing them that arrest warrants have been issued against them. The messages also asked recipients to download an APK file, which carried the Bank Negara logo and name.
In June, a fake ScamShield app was targeted at Singaporeans. The fake app fraudulently bears the official ScamShield app logo, which is an official anti-scam product developed by the National Crime Prevention Council and Open Government Products. The scammer would recommend the victim download the (fake) ScamShield app, on the pretext of getting the victim to safeguard against scams and to make a report in the ScamShield app.
Most trojans, including Pink WhatsApp, will request additional permissions, which is a tell-tale sign of malware.
From Pink WhatsApp to Sharkbot
Another example of an infamous trojan app highlighted by Sysmans is Sharkbot, a mobile banking trojan.
Sharkbot was labeled “a new generation of mobile malware”, because of its ability to perform Automatic Transfer System (ATS) attacks. ATS is an advanced technique, which enables attackers to auto-fill fields in legitimate mobile banking apps and initiate money transfers from the compromised devices.
Like all other trojans, Sysmans also pointed out that Sharkbot masquerades as a seemingly legitimate app, including media players, live TV apps and data recovery apps. Once installed, Sharkbot launches a Permissions Escalation attack that bombards the user with fake pop-ups until they grant the fake app access to their phone’s Accessibility Services.
“In all cases, the fake applications served as a gateway for fraudsters to collect personally identifiable information (PII) to make unauthorized transactions from the victim’s bank accounts or credit cards,” he said.

Most trojans, including Pink WhatsApp will request additional permissions, this is a tell-tale sign of malware. (Image source – Shutterstock)
The problem with malicious apps
One of the biggest problems with malicious apps is that they can affect other apps on the device as well. Sysmans explained that this was how all on-device malware works. Once a malicious app is installed on the device, the malware in the app will request additional permissions on the device. Once access to administrative privileges is enabled, the malware can launch an attack on other apps on the device.
What’s more concerning is that the malware could remain dormant and monitor the device in the background until it finds useful information to exploit, such as banking credentials. In fact, Sysmans mentioned that today’s advanced malware is often hidden, which helps it stay undetected for a longer time.
As such, WhatsApp themselves have taken security measures by banning user accounts that are found to be using unofficial third-party apps that are caught trying to harvest information.
“Pink WhatsApp was disseminated through an automated distribution of messages to all contacts of an infected account. By implementing a ban, WhatsApp is trying to protect other users by containing the malware and reducing the spread,” added Sysmans.
The video below shows how to deal with malicious apps like Pink WhatsApp.
Pink WhatsApp is just one of the many vulnerabilities for mobile devices
Many vulnerabilities in mobile devices can be easily targeted. While Pink WhatsApp is a concern, cybercriminals can also target mobile devices through numerous other methods. This includes malware in emails accessed on mobile devices as well as through an unsecured network or WiFi that the mobile device is connected to.
Sysmans suggests that beyond practicing good digital hygiene such as setting strong passwords, users should never root or jailbreak their device because most malware depends on rooting and jailbreaking for the exploits to be most effective.
“Consumers should avoid using unknown or untrusted public Wi-Fi networks as these might expose them to potential man-in-the-middle attacks. If one must use public Wi-Fi, consider using a virtual private network (VPN). Individual consumers may not be able to tell if their app or device has been compromised, so it is up to brands to protect their applications. Users trust the applications they use on a daily basis, and it’s up to the app publisher to meet those expectations to keep the bad guys out,” added Sysmans.
With the ever-changing threat landscape, Sysmans also suggests app publishers use a cyber security solution that meets their needs of today and allows them to easily change their security model to protect against new threats and attacks.
“With the overwhelming demand for security, anti-fraud and malware protection in mobile apps, businesses need to facilitate DevSecOps in their CI/CD pipeline. Ideally, developers should not have to compromise their workflow to accommodate cybersecurity solutions in their apps. And cyber teams should have visibility and control over the security model implemented in their app. The only way to achieve this and still be able to release apps in a rapid and agile way is to use a no-code mobile cyber defense automation platform,” he concluded.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


