
The latest security breach at Okta is due to a compromise of the support system, granting an attacker access to sensitive files uploaded by Okta’s customers. Photo: Shutterstock
Okta’s repeated security breaches and delayed disclosures
- The latest security breach at Okta is due to a compromise of the support system, granting an attacker access to sensitive files uploaded by Okta’s customers.
- 1Password, BeyondTrust, and Cloudflare detected and stopped the intrusions before affecting their customers, but Okta took weeks after being notified before publicly disclosing the breach.
Okta, which forms a critical part of cybersecurity systems at major corporations, confirmed last week it suffered a breach on its support system. Although Okta’s official statement suggests that the breach may be insignificant, what has raised concerns among observers and customers is the company’s communication, or rather, the lack of it.
It’s not the first time Okta has shown a lack of urgency in dealing with a system compromise that has put an undisclosed amount of customer’s data at risk. Okta’s response has faced severe criticism, as the company’s value has suffered. Investors reduced Okta’s market capitalization by approximately US$2 billion in the week following the public disclosure of the security breach.
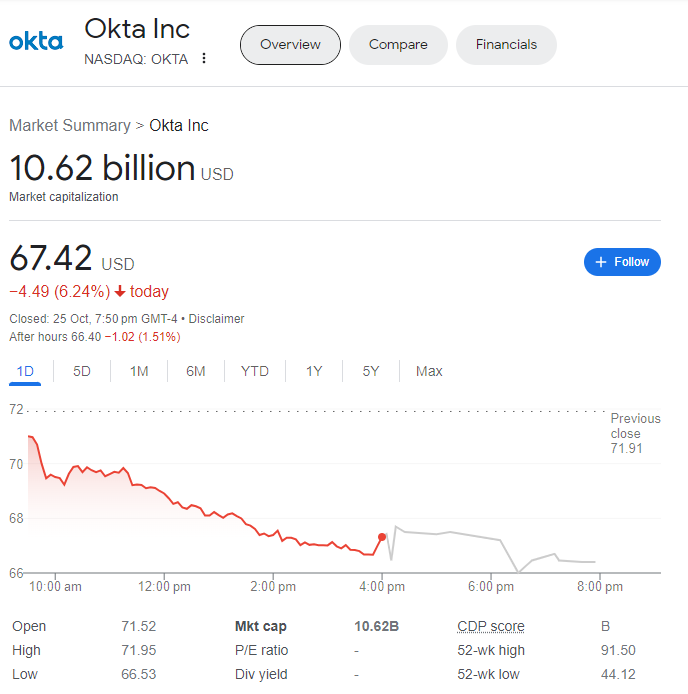
Okta’s share price as of Oct 26, 2023, 12:50pm (GMT+8).
What and when did it happen?
The recent security incident directly impacted Okta’s in-house customer support service rather than a service provided by a third-party partner. In this instance, the attackers employed stolen login credentials to breach an Okta support account. Subsequently, they used this access to steal cookies and session tokens, typically to grant customer support providers access to clients’ systems for problem-solving.
Armed with these access tokens, the attackers were able to compromise Okta customer accounts directly. The first one to notice was password manager 1Password, an Okta customer. In a statement this week, 1Password said that it had notified the company as early as September 29 of suspicious activity that ultimately was tied to the support system incident.
Then, on October 2, when BeyondTrust, an identity and access management company, highlighted that it identified suspicious activity in its Okta administrator account. Subsequently, BeyondTrust promptly informed Okta about the matter on the same day. Unfortunately, according to a statement by BeyondTrust, “having received no acknowledgment from Okta of a possible breach, we persisted with escalations within Okta until October 19.”
Source: X
Only then did Okta security leadership notify BeyondTrust that they had experienced a breach and that BeyondTrust was one of their affected customers. Before the response from Okta on October 19, a day before, internet infrastructure company Cloudflare also revealed that it had detected a similar incident in its Okta systems and notified the company as well. “This is the second time a breach of Okta’s systems has impacted Cloudflare,” a group of Cloudflare engineers wrote on Friday.
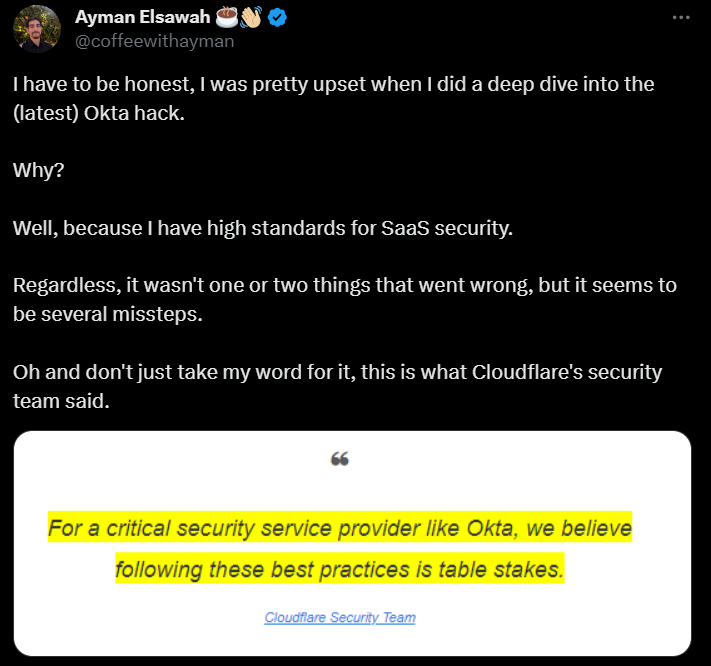
They shared a list of recommendations for how Okta can improve its security posture: “Take any report of compromise seriously and act immediately to limit damage. Provide timely, responsible disclosures to your customers when you identify that a breach of your systems has affected them. Require hardware keys to protect all systems, including third-party support providers.”
Cloudflare aptly noted that they view taking protective steps like these as “table stakes” for a company like Okta that provides such crucial security services to many organizations. Okta is considered a company with critical solutions, considering it offers essential digital services to a substantial and prominent customer base, making them inherently attractive targets for cyberattacks.
How many times has Okta fallen victim to a security breach?
Considering Okta handles logins for more than 100 million users, including large companies, it can be a convenient single entry point for hackers seeking to infiltrate multiple organizations. Unfortunately, the identity management company has had several security issues recently.
In the last two years alone, four incidents were brought to light. Starting in January 2022, when the Lapsus$ data extortion group gained access to its administrative consoles, Okta only disclosed that some of its customers’ data was exposed two months later. One-time passwords (OTPs) delivered to Okta customers over SMS were also stolen by the Scatter Swine threat group (aka 0ktapus), which breached cloud communications company Twilio in August 2022.
In the same year, Okta-owned authentication service provider Auth0 disclosed in September that some older source code repositories were stolen from its environment using an unknown method. Then came December when Okta revealed its source code theft incident after the company’s private GitHub repositories were hacked.
The recent breach at Okta is especially worrisome because it resembles a security incident the company suffered in 2022. In that case, attackers compromised a subprocessor that Okta had relied on for customer support tasks.
Adam Chester, a senior security consultant at TrustedSec, told Wired: “What I find surprising in this case is that, after the 2022 breach, you’d think Okta would be on high alert for any externally exposed systems or personnel who may be targeted—and yet something has happened again.”
In this latest episode, Okta had only gone so far a to admit that “Okta Security has identified adversarial activity that leveraged access to a stolen credential to access Okta’s support case management system.”
Without diving deeper into details, CEO David Bradbury assured “all customers impacted by this have been notified.” In short, the updates shared by the likes of 1Password, BeyondTrust, and Cloudflare had been far more substantial than the ones by Okta itself.
What’s next for Okta?
Considering incidents are being dealt with the same way one too many times, analysts mulled over the possible negative impact on Okta stock and the cybersecurity firm’s sales pipeline. “We now have concerns this could have a negative impact on the quarter and the pipeline,” Wells Fargo analyst Andrew Nowinski said in a report.
What’s most concerning for Wells is that Okta was unaware of the breach and did not have the internal capabilities to detect this behavior. “They were notified of the potential breach by a customer (Beyond Trust) and still took approximately two weeks to make a public disclosure,” he added.
In a separate report, Raymond James analyst Adam Tindle said, “Another security incident could cause customers to question their identity/access provider and rethink renewals/expansion as Okta looks to move into adjacencies.”
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


