
The increase of ransomware incidents in Australia. (Source – Shutterstock)
Australia’s cybersecurity crisis: Organizations need to stop paying ransoms
- Over 94% see a rise in 2023 ransomware threats.
- 78% may pay a ransom for data recovery and business restoration.
A recent study commissioned by Cohesity reveals that many companies in Australia and New Zealand are inadequately equipped with the essential cybersecurity strategies and abilities to effectively combat the rising tide of cyber threats like ransomware and ensure business continuity. The pace of their efforts in improving cyber resilience is far behind the rapidly evolving cyber threats. The lack of data security and recovery technologies limits their eligibility for cyber insurance and amplifies the consequences of successful cyber attacks.
When juxtaposing the cybersecurity landscape of 2023 with that of 2022, a staggering 94% of survey participants claimed that the danger of ransomware attacks to their industry had escalated in 2023. What’s more worrisome is that more than half (56%) confirmed a ransomware attack had hit their company in the previous six months, while nearly one out of ten (9%) were uncertain.
Survey participants also acknowledged that their firms’ cyber resilience and data security capabilities were not up to speed. 79% voiced their apprehensions regarding their company’s cyber resilience strategy and its ability to confront today’s cyber threats and challenges.
Ransomware still causing havoc in the cybersecurity landscape
The recent data breaches happening in Australia, particularly among large corporations, have raised serious concerns. One major incident occurred in March 2023, when Latitude, an Australian personal loan and financial service provider, suffered a data breach that affected more than 14 million individuals in Australia and New Zealand. Although the initial disclosure said only 328,000 customers were affected, that number quickly climbed to 14 million after further investigation.
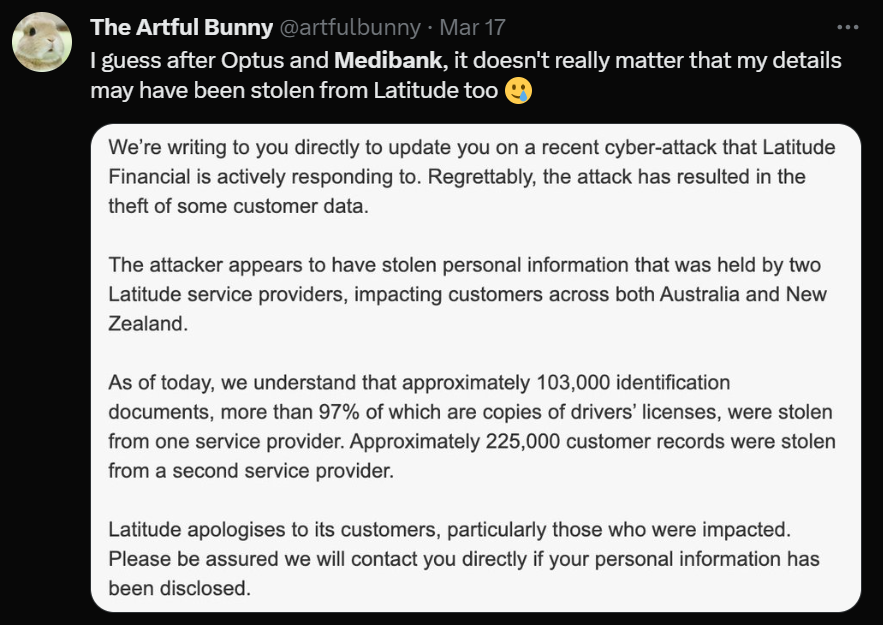
A Twitter user named, @artfulbunny, commented how their data was being stolen. (Source – Twitter)
This incident involving Latitude was one of the most significant breaches in Australia’s recent past and followed a succession of high-profile attacks, including those on Optus and Medibank. The breach occurred due to stolen employee credentials, which provided unauthorized access to Latitude’s customer data, including full names, physical addresses, phone numbers, and passport numbers.
The data was predominantly from 2005, leading to questions about why companies retain customer records beyond the mandatory seven-year period. This situation has even prompted the government to contemplate expanding the mandate of federal cyber agencies to intervene when private companies come under attack.
The Australian health insurance behemoth, Medibank, was also targeted in a major data breach that compromised the personal details of 9.7 million customers. The attack was purportedly orchestrated by a notorious ransomware group based in Russia, the REvil ransomware gang.
The privacy violation was first noticed when REvil posted 6GB of raw data samples on a dark web blog, implying that they possessed even larger data sets to release and demanded a US$10 million ransom. This data encompassed names, birthdates, passport numbers, medical claims data, and medical records.
Despite suffering one of the most extensive data breaches in Australian history, Medibank refused to pay the ransom. Although the data is believed to have been entirely released on the dark web, there have been no reported incidents of identity theft or financial fraud. Medibank has also advised customers to remain alert to credit checks and phishing scams and has invested substantially in its cybersecurity measures. It was even reported by ABC News that the Medibank data hack was far worse than Optus breach. Watch the video below:
The frequency of data breaches in Australia, especially within the financial and healthcare sectors, is increasing. In response, the Australian government is revamping its cybersecurity protocols and policies to bolster resistance against nation-state threats.
However, Australian businesses can’t solely depend on government-led cybersecurity initiatives. The Australian Signals Directorate (ASD) has conceded that the proposed security frameworks merely set a minimum standard for security. It remains incumbent upon individual businesses to further raise this standard by implementing additional data breach prevention measures.
Battle against time
Maintaining business continuity in the face of cyber threats is crucial. The ability of organizations to recover data and restore business operations quickly is limited. When queried about how long their organization would need to restore data and business processes following a cyberattack, an overwhelming 99% of participants stated they would require more than 24 hours, 80% suggested it would take over 4 days, and nearly half (47%) claimed more than a week would be necessary.
Seven out of ten respondents (71%) lacked complete confidence that their company could retrieve their data and crucial business operations in the event of a comprehensive cyberattack. When diving deeper into perceptions of cyber resilience and actual data recovery capacities, 95% of participants acknowledged their organization might consider paying a ransom. Almost 4 out of 5 (78%) went further, confirming their organization would indeed surrender to ransom demands if it guaranteed swift restoration of data and resumption of business activities.
Michael Alp, Managing Director, Cohesity Australia & New Zealand, asserted that organizations cannot afford to be offline and halt operations, especially for more than a day.
“The stark reality is that many organizations are vulnerable to leverage from cyber criminals because they are incapable of rapidly recovering their data and business processes when necessary,” Alp remarked. “Therefore, it’s no surprise that less than 5% of respondents said their organization would not consider paying a ransom to maintain business continuity and that the vast majority of respondents believe their organization would pay cybercriminals a ransom.”
To pay or not to pay
Regarding ransom payments, the Australian Cyber Security Center (ACSC) sternly advises against conceding, as they may sometimes be deemed illegal. It is a serious offense to support criminals or financially fund criminal activities. Hence, ransom payments could be considered illegal and should be avoided, as outlined in the Criminal Code Act 1995, and the Anti-Money Laundering and Counter-Terrorism Financing Act 2006.
Given these regulations, Australian businesses must establish advanced cybersecurity measures to evade situations where ransom payments are demanded. Nevertheless, the success of ransomware attackers and the increasing frequency of attacks on Australian companies have stimulated the proposition of a contentious Labor bill. This legislation would obligate Australian organizations to report any ransom payments made if enacted.
The Ransomware Payments Bill 2021 requires victims of ransomware attacks to notify the Australian Cyber Security Centre (ACSC), ideally before a ransom payment is made. The aim is to diminish compliance with cybercriminals’ demands by presenting victims with alternative solutions they might not have previously considered. An advantageous side effect of this support is the provision of valuable intelligence to law enforcement agencies that could assist in tracking down criminal groups.

Should organizations pay ransom? (Source – Shutterstock)
Noteworthy details include the ransom amount demanded (typically specified in bitcoin), the details of the cryptocurrency wallet where the ransom payment should be made, and indicators of compromise. The proposed legislation doesn’t define the consequences of non-compliance, but it does warn that a failure to notify the ACSC will result in a penalty.
In response to emerging nation-state threats, the Australian government is aligning its cybersecurity regulations with the United States’ new stance. This has resulted in significant changes to the expectations for how Australian businesses should react to cyberattacks.
The need for anti ransomware solutions and comprehensive cybersecurity posture insights
When asked about the main obstacles hindering their organization’s recovery from a successful cyberattack, participants cited a lack of coordination between IT and security (33%), a lack of timely and detailed alerts (32%), and the absence of a recent, clean, and unaltered copy of data (30%). Moreover, less than half expressed confidence in the security and protection of all their data stored in the cloud (45%) or at the edge (38%), with only one in six respondents (17%) expressing confidence in on-premises data security and protection.
As a result, 88% of participants voiced the need for data and cybersecurity vendors to collaborate in providing comprehensive and integrated anti-ransomware solutions. Additionally, 91% of respondents felt their organization would benefit from a data security and management platform that offers insights into their overall security posture and cyber resilience.
The urgency of having robust data backup and recovery services is highlighted by the fact that they’re critical for qualifying for cyber insurance. Not all solutions meet this criterion. While 75% of respondents confirmed their company has cyber insurance, nearly half (48%) reported it is now more challenging to obtain cyber insurance than in 2020. The three most crucial technologies or capabilities needed to secure cyber insurance were identified as “strong encryption” (39%), Multi-Factor Authentication (37%), and the “ability to verify the integrity of backups” (34%).
Alp highlighted the need for IT and SecOps to jointly manage their organization’s cyber resilience outcomes to identify sensitive data and effectively protect, detect, respond, and recover from cyberattacks. He stressed that dependence on traditional backup and recovery systems, which lack modern data security capabilities, is a risky approach in the face of today’s sophisticated cyber threats.
“Organizations should opt for data security and management platforms that harmonize with their existing cybersecurity solutions and offer visibility into their security posture to enhance cyber resilience,” he concluded.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


