
Ransomware is found in 150 different countries and will cost victims US$ 265 billion by 2031
Found in 150 countries, ransomware to cost victims US$265 billion by 2031
- Ransomware will cost its victims more, around US$265 billion annually, by 2031.
- Bitdefender say that they found ransomware from 150 different nations.
Ransomware attacks have dominated headlines over the past year due to high-profile breaches affecting businesses worldwide. The major attacks in 2022 were a part of criminality on a global scale.
With the sharp rise in remote working, ransomware attacks have significantly increased. It is estimated that the threat will cost its victims around US$265 billion annually by 2031. To further protect against these ongoing criminal operations, immediate action is needed in response to these cyber threats.
How do ransomware attacks happen?
Bitdefender recently released its “November Threat Debrief,” a monthly series that analyzes threat headlines, trends, and research from the prior month. It also has a Ransomware Report that lists the top ransomware families identified, the countries affected, and the top Android trojans for October.
According to a report, spear phishing attacks are often utilized as the primary attack vector, and ransomware infection is frequently the last link in the kill chain. For this report, Bitdefender examined malware detections gathered in October 2022 from their static anti-malware engines. Opportunistic adversaries and some Ransomware-as-a-Service (RaaS) groups make up a bigger percentage than groups who are pickier about their targets Since they choose volume above better value.
This data represents only ransomware detections, not infections.
Bitdefender analyzed malware detections from October 1 through October 30. They discovered 189 ransomware families in total. Depending on the ongoing activities in various nations, the number of discovered malware families can change each month. The three most prevalent families discovered—WannaCry, GandCrab, and Cerber—accounted for 74% of all detections. REvil/Sodinokibi also made an appearance.
With the discovery of so many ransomware families, it was tested in numerous countries. Bitdefender claims that they found the threat from 150 different nations in their dataset this month. The threat posed by ransomware is still present practically everywhere. Numerous attacks remain opportunistic, and the population’s size and frequency of detections are associated. Australia ranked eighth on the list, contributing 5%, while the top three countries—the United States, Brazil, and Iran—contributed a combined 52%.
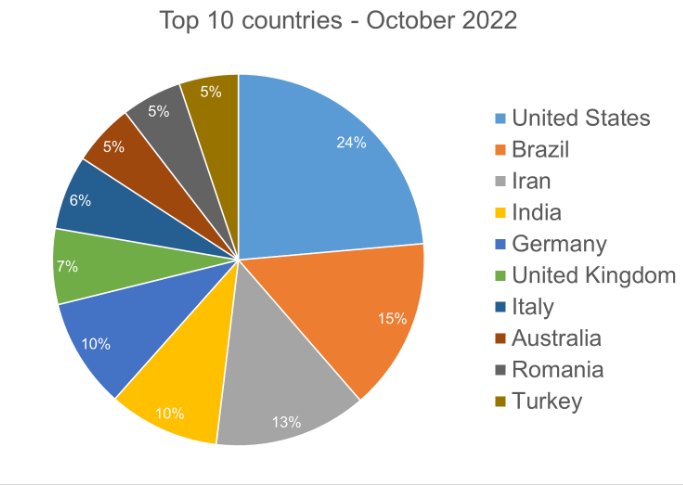
Top 10 countries most impacted by ransomware. (Source – Bitdefender)
Users aren’t aware of homograph phishing attacks
The concept behind homograph (also referred to as homoglyph) phishing attacks is to use similar characters to impersonate another website. The homograph attacks based on international domain names (IDN) can be indistinguishable from domains they are spoofing, even though most of them are recognizable by end users with proper training (for example, g00gle.com).
The top 10 websites that people fall for phishing scams are shown below.
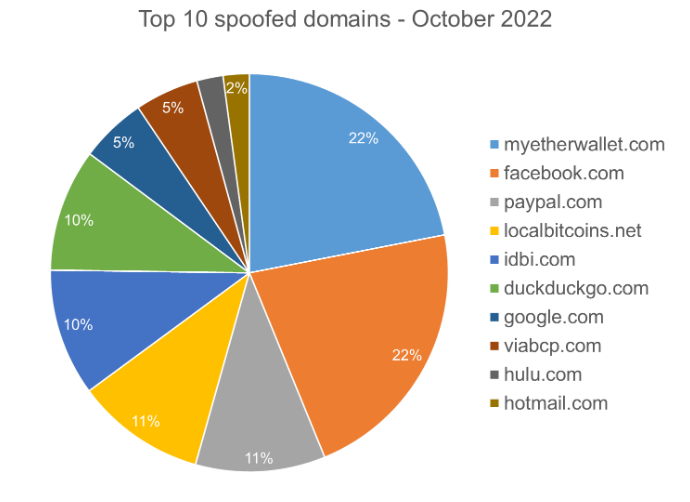
Top 10 most common targets for phishing sites. (Source – Bitdefender)
What do ransomware attacks mean for APAC?
Even though only one APAC country is mentioned in the report as having to deal with distinct ransomware families, it is still essential to underline that the region needs to step up its cybersecurity efforts.
Barracuda researchers noticed a substantial rise in ransomware attacks targeting all industries between August 2021 and July 2022 after examining 106 well-known incidents worldwide, including Southeast Asia.
Unexpected challenges may arise for businesses from any industry or country due to these ransomware attacks. APAC countries are known to face a greater potential threat from cyber-attacks than other nations worldwide, mainly because of the region’s rapid and extensive increase in digital use and connectivity.
According to Statista, China accounted for 34.4% of internet users in Asia as of July 2022, followed by India with 28.4%.
When analyzing the region’s increase in internet users, it’s worth noting that the cyber risk is further increased by the large portion of the digitalization surge made up of users who have no prior knowledge of viruses, malware, phishing scams, or other threats. Therefore, every employee and individual must receive training to develop an efficient cybersecurity venture.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


