
Australia increases penalties for data breaches after Optus, Medibank hacks.Source – Shutterstock
Cyber threats are smart, that’s why they are on the rise
- The average DDoS attack lasted 3,000 minutes, an increase of 100 times.
- With smart attacks making up almost half of all attacks, the percentage almost shattered the four-year record.
Distributed Denial of Service (DDoS) is undoubtedly one of the popular cyber threats that cybercriminals frequently use. DDoS poses a serious risk to the ongoing operation of businesses. The availability of the Internet and web-based programs and services has become as crucial as the availability of electricity as businesses have grown increasingly reliant on them.
In fact, availability is crucial to maintaining an organization’s “good image” because it has a direct impact on client satisfaction and brand reputation. A disruption to business continuity could have a detrimental effect on a company – such as network downtime.
According to Gartner, downtime costs businesses more than $5,600 every minute. The size and breadth of a company will also play a role in this. Millions of dollars can be lost by large companies in a single hour. For just one hour of downtime, even SMBs can suffer losses of up to $540k.
There is no guarantee that anyone is safe given how severe cyber threats are nowadays. It’s interesting to note that according to Kaspersky, DDoS attacks reportedly reached a new level in Q2 2022 as the percentage of smart attacks and the average duration both sharply increased. The average duration of a DDoS attack increased 100 times in comparison to the previous year, reaching 3,000 minutes.
Furthermore, with smart attacks making up almost half of all attacks, the percentage nearly shattered the four-year record. Experts predict a rise in DDoS activity in general, particularly in light of the recent collapse of cryptocurrencies.
Average DDoS session duration
A typical attack in Q2 2022 lasted 3,000 minutes, or two days. It is 100 times longer now than it was in Q2 2021 when an attack normally lasted 30 minutes. The Q2 number also shows an increase—by three times—when compared to Q1 2022, which was characterized by DDoS sessions lasting longer than ever before due to hacktivist activity.
In the most recent quarter, several attacks lasted for days or even weeks. A record was established with an attack that lasted 41,441 minutes, or just under 29 days.
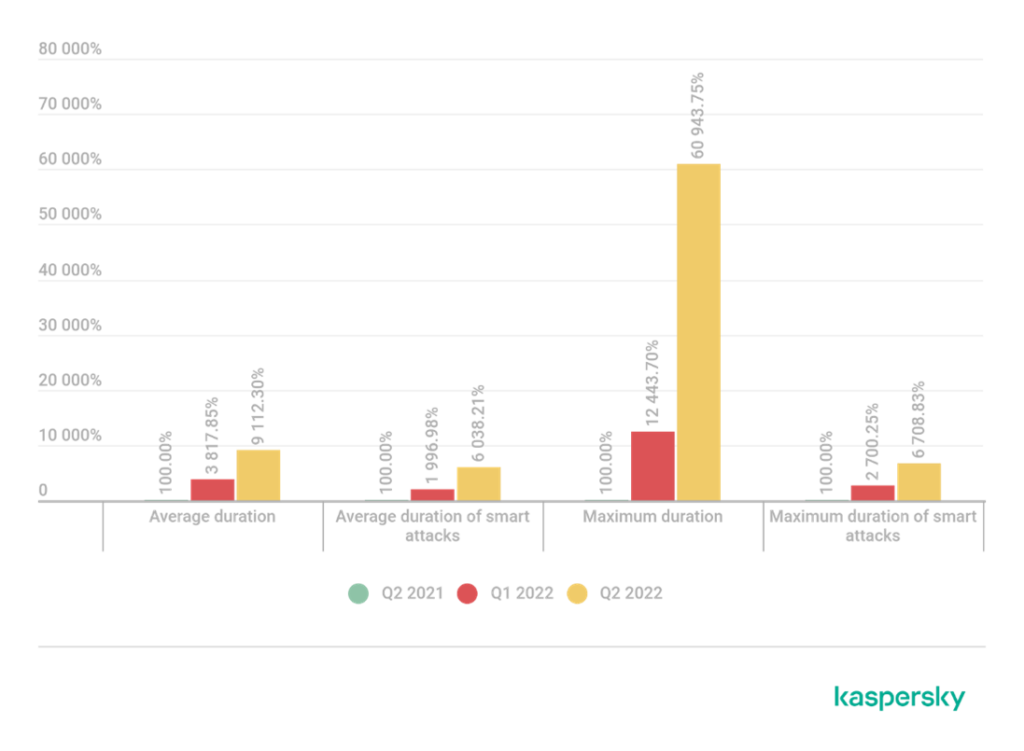
A comparative duration of DDoS attacks: Q2 2022 and Q2 2021 as well as Q1 2022. Data for Q2 2021 is taken as 100%
Smart cyber threats looking to break a record
In Q2 2022, every second attack that Kaspersky’s products discovered was smart, indicating that its organizers had done a lot of careful planning. This quarter saw an almost record-high level of smart attacks—nearly 50% of all attacks. It’s surprising to see data that high in a year that has been “hot” in terms of DDoS activity because the record-high share was established four years ago when the DDoS business was in a slump.
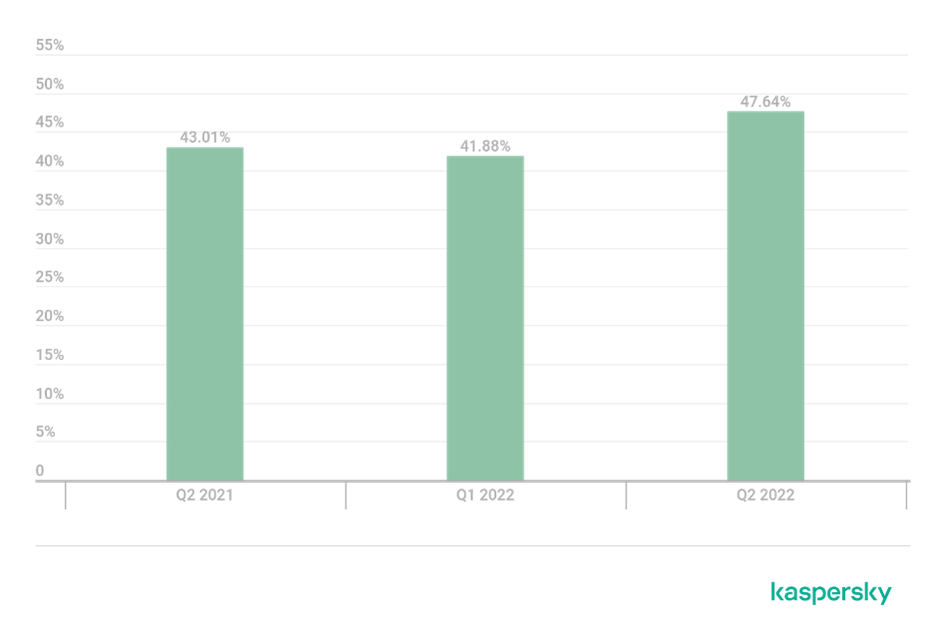
The share of the smart DDoS attacks: Q2 2022, Q2 2021 and Q1 2022
Relationship between cryptocurrency and the DDoS market
DDoS attacks were less frequent in the second quarter than they were in the first. It is common for DDoS activity to decrease as summer approaches, according to experts. According to the Kaspersky DDoS Intelligence system, the dynamics of the number of DDoS attacks within the quarter this year didn’t follow this usual tendency. After declining at the end of Q1, botnet activity progressively grew during Q2, reaching a peak in June as opposed to April. This is consistent with cryptocurrency price declines, which frequently cause the DDoS market to heat up.
“The collapse of cryptocurrencies began with the plummet of the Terra (Luna) and has only been gaining momentum since. Various factors indicate that the tendency may continue, for example, cryptominers are selling off farms at low prices to gamers. This can lead to a surge in global DDoS activity,” Alexander Gutnikov, a security expert at Kaspersky explains.
DDoS attacks are not only getting worse, but they are also getting more frequent. Due to the rise in DDoS attacks, almost every company will experience one at some point. As a result, planning for this attack type should be at the top of the organization’s security to-do list.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


