
Source – Microsoft
The growing attack surface is in need of threat intelligence solutions
- Microsoft Defender Threat Intelligence gives enterprises direct access to real-time data from Microsoft’s security signals to more actively search for threats in their surroundings.
- External Attack by Microsoft Defender Surface Management enables security teams to identify unidentified and unmanaged resources that may serve as possible points of entry for an attacker.
Internet of things (IoT) devices, 5G networks, and other distributed computing initiatives are rapidly expanding, creating a much wider attack surface for cybersecurity teams to defend. Hence threat intelligence tools are needed because it enables individuals to make faster, more informed, data-backed security decisions and shift from being reactive to proactive in the fight against threat actors.
The threat landscape has changed so significantly that more cyberattacks are being launched. For instance, according to IoT World Today, there were approximately 1.51 billion breaches of Internet of Things (IoT) devices from January to June of 2021, up from 639 million in 2020.
Organizations are advised to move beyond traditional approaches in order to capitalize on the commercial advantages of cutting-edge technologies like AI, cloud computing, 5G, and others without placing themselves in further danger from the expanding threat surface.
Therefore, Microsoft has introduced two new security products – Microsoft Defender Threat Intelligence and Microsoft Defender External Attack Surface Management – to give organizations a deeper context into threat actor activity, assist them in securing their infrastructure, and decrease their overall attack surface.
According to Vasu Jakkal, Corporate Vice President of Security, Compliance, Identity, and Management at Microsoft, any device connected to the internet is vulnerable. For businesses, the key to fostering resilience is comprehending the gaps that may give rise to these vulnerabilities.
“We recognize the importance of working together as a security community to help protect the planet from threats. These new threat intelligence offerings expand our growing security portfolio, offer deeper insights into threat actors and their behaviors, and help security teams accelerate identification and prioritization of risks,” he commented.
Dive deep into Microsoft’s threat intelligence technologies
Damages have skyrocketed and the threat landscape is more complex than ever. Microsoft currently monitors over 250 distinct nation-states, cybercriminals, and other threat actors, as well as 35 different ransomware families. More than 43 trillion security signals are processed and analyzed daily in its cloud.
Microsoft has been able to offer customers unparalleled visibility into threat actor activities, behavior patterns, and targeting due to the massive quantity of intelligence it gathers from its platform and products and its acquisition of RiskIQ in 2021. Customers can map their digital environment and infrastructure to see their business from the perspective of an attacker, and this outside-in perspective offers even more insightful data that enables businesses to identify malicious behavior and secure uncontrolled resources.
Every day, Microsoft Defender Threat Intelligence maps the internet, giving security teams the knowledge, they need to comprehend adversaries and their attack strategies. Customers now have access to a repository of unfiltered threat intelligence that lists enemies by name, correlates their tools, strategies, and procedures, and displays live updates as new data is gleaned from Microsoft’s security signals and experts. This enables enterprises to uncover the tactics used by attackers and threat families, assisting security teams in discovering, eliminating, and blocking any tools that their adversaries may have buried within the company.
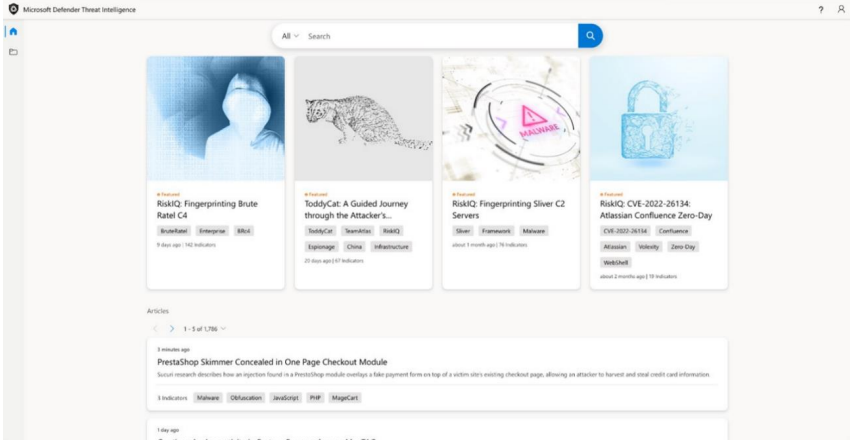
Microsoft Defender Threat Intelligence home screen featuring adversary articles for users to read
While Microsoft Defender External Attack Surface Management continuously scans the internet and its connections, it creates a comprehensive inventory of the environment of a business, identifying all internet-facing resources, even agentless and unmanaged ones. Continuous monitoring prioritizes emerging vulnerabilities without the use of agents or credentials. Through the use of their security information and event management (SIEM) and extended detection and response capabilities, enterprises are able to take the required precautions to reduce risk and secure the management of these unidentified resources, endpoints, and assets.
In order to track threat actors more closely and better understand their behavior over time to counter these threats, Microsoft continuously leads the industry in aggregating signal and threat intelligence across the behavioral estate.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


