
Cyberattacks were everywhere in 2017, as they will be in 2018. Source: Shutterstock
2017: A watershed year for cybersecurity
THOUGH we will come to characterize 2017 with many words and many concepts over the coming months, this year will probably be remembered as the year when warfare came to the cyber sphere in earnest.
We’ve seen the effects of huge cyberattacks such as the WannaCry ransomware attack, the fall-out from the NotPetya event and the ongoing struggle surrounding Equifax. Suffice to say, this year has been a drawn-out affair of learning not just about those who would inflict harm on our systems but also our capabilities to protect ourselves.
One could make the argument that we’re not doing a great job.
“It’s a constant battle between security and cybercrime and unfortunately, we have been playing catch up for years.” said Bill Taylor-Mountford, the vice-president for LogRhythm’s Japan and Asia Pacific branches, to Tech Wire Asia in an email interview.
The issue of cybersecurity has been neglected for so long – if not relegated to back-room tinkers working furiously against time in an ever-evolving industry – that we are all now playing catch-up. And what a time to be doing so! 2017 has, if nothing else, proven just how unprepared we all are.

Bill Taylor-Mountford. Source: LogRyhthm
Taylor-Mountford spoke about the kinds of trends and patterns that we can observe from the events that took place in the last year, as well as what we can possibly expect in the coming months. According to him, we will definitely begin to a significant increase in cyber attacks in the next year, a reality that will be fueled by three things: the potential profits of cybercrime, access to cybercrime tools and a rising trend of state-backed attacks.
“Cybercrime has become such a lucrative business, and the marketplace and strategy [are] evolving,” he said.
Taylor-Mountford explained that though direct methods of cyberattack are still popular – these include ransomware, or malware used to steal data, assets or cryptocurrency — there is a rising trend of events targeted at “indirect gains”, whereby attacks extort money.
“It’s getting easier for cybercriminals to gain access to advanced tools and services. Where in the past, users kept largely to themselves, we are seeing more individuals working together and even selling their work as services.”
He said that we would likely see a rise of “DDoS-as-a-service” products become more commonplace as more hackers begin selling their tools to bad actors.
Is this the age of the state-sponsored attack?
One thing became clear this year and that’s the fact that we’re rapidly entering a new form of warfare, one that takes place not on the battlefield with guns and soldiers, but on the digital frontlines where keyboards and firewalls are the only things standing between us and the loss of valuable information. It cannot be stressed enough that the “new gold” coveted by black hats everywhere is data – data is more important than ever and it can cause harm in ways we could never have imagined.

The North Korea flag flutters next to concertina wire at the North Korean embassy in Kuala Lumpur, Malaysia. Source: Reuters
This year, we saw the rise of the state-sponsored attack, with players such as North Korea, Russia and Vietnam playing starring roles. Stories have spread across the web about a small group of actors – as well as lone wolves – or industrialized efforts to breach security solutions. Taylor-Mountford said that though state-sponsored attacks are on the rise, the likeliest targets will be companies.
“The misconception is that state-sponsored attacks happen between governments, trying to steal military, financial or political data,” he said.
“In reality, there are many organisations that hold sensitive information, with much weaker cybersecurity. These are the organisations that will be the targets of state-sponsored attacks.”
He went on to say that digital warfare has been in the works for several years now – think of all those blockbuster films that are now focused on cybercrime – though most attacks are still pretty under the radar. Few large-scale events have been conclusively correlated with state agents, but researchers have ways of identifying certain signs.
“What we expect to see in 2018, is more of such state-sponsored attacks (such as the cyberwar between the US and North Korea) being intentionally public,” he said, adding that other countries will begin engaging in cyber-battles.

Credit cards, a chain and an open padlock is seen in front of displayed Equifax logo. Source: Reuters
Taylor-Mountford gave the example of North Korean Supreme Leader Kim Jong Un, whose affinity for video games may have been the inspiration behind the massive 2014 Sony Entertainment data breach. Game consoles, such as the PlayStation, store important interaction data, such as recent games played, time logs, and current activities. He also said that we’d likely see more public investment being poured into security resilience as war moves further and further into the digital landscape.
Awareness is on the rise
“What we have noticed, however, is that military powers around the world have begun to understand how important it is to invest in cyber resilience and we are seeing a new breed of soldiers that are trained specifically to defend against such threats,” he said.
“For example, Singapore’s Defence Cyber Organisation, its military’s cybersecurity arm, recently announced its Bug Bounty Programme, inviting white hat hackers to find vulnerabilities in its web-facing systems.”
Most modern countries have already begun working on the issue in earnest – Malaysia tabled a cybersecurity law this year, while Singapore is still working on theirs. China’s controversial laws are probably the most sweeping of the Asian nations, though many more are likely to follow. However, he noted, that a lot more effort can be made with regards to the discovery and disclosure of such attacks, as well as post-event remediation.
“Of the notable data breaches we heard of this year, Yahoo, Uber, Equifax, Imgur, and even the Malaysian mobile users data breach, the one thing they all had in common was that the data breach had occurred years ago,” he said.
“Some of the exposed data were extremely sensitive and could have been easily used as a launch bed for more sophisticated attacks, yet it still took years to discover and rectify the problem. That is frankly unacceptable.”
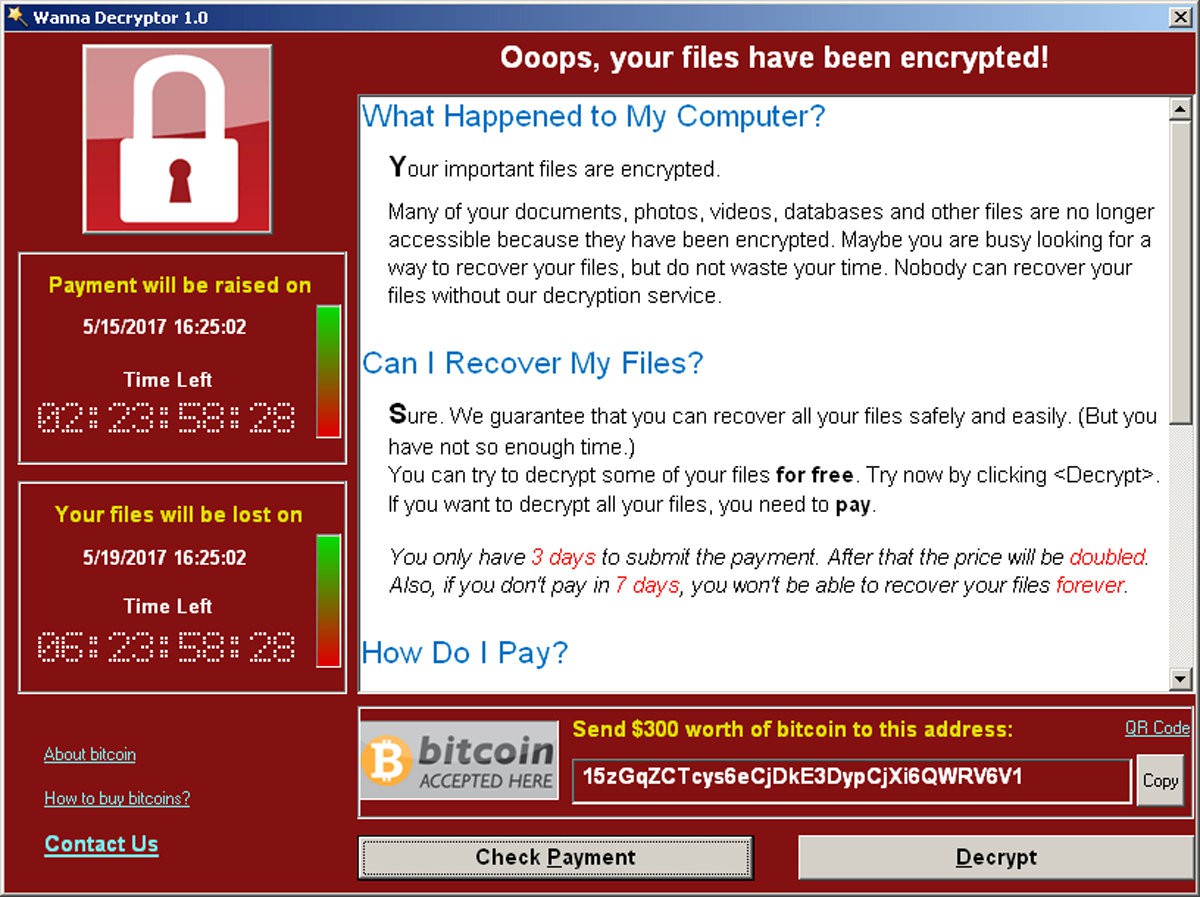
A screenshot shows a WannaCry ransomware demand, provided by cyber security firm Symantec. Pic: Reuters
He said that more effort needed to be diverted to Internet of Things (IoT) networks and systems, especially with regards to new technologies that relate, such as autonomous vehicles. These are all networks whose exposures can and will be exploited by hackers, and which must be safeguarded if we’re to move any further in our smart city efforts.
With regards to efforts for the new year, Taylor-Mountford said that businesses and organizations should already have basic cyberdefense plans already in place and should build on top of them with good hygiene training and practical steps.
“Ultimately, even with the most robust cyber defenses, determined cybercriminals may still be able to exploit vulnerabilities to hack into the network,” he cautioned.
“Organisations need to account for this eventuality and ensure they are able to quickly detect and respond to these threats effectively.”
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network








