
The national central database hub of Malaysia, on launch. (Image source – X).
Here’s how Malaysia’s central database hub, Padu can be compromised by cybercriminals
- Malaysia launches Padu, its central database hub.
- Security concerns cloud some of the authentication features on the hub.
- Government insists the database is safe for public use.
One of the biggest problems with data collected by government agencies is that it is often stored in silos by the respective agencies. Accessing all this data through a single platform or hub would ideally be the most effective way to gain comprehensive insights.
The Malaysian government has just launched the country’s national central database hub. Called Padu, the system will contain individual and household profiles of citizens and permanent residents in the country.
The entire central database hub, developed locally, took around six months to complete. Since its launch, thousands of Malaysians have rushed to register their accounts, leading to such high registration traffic that the system briefly struggled to cope with the demand.
While most Malaysians were impressed that the government had finally launched a system consolidating all necessary information in one location, there were concerns about the security features of the Padu system. Comments on social media highlighted weaknesses in some features, particularly in user registration processes.
Rafizi Ramli, Malaysia’s Economic Minister who is overseeing the database, said that the government is aware of the cybersecurity concerns and has taken the measures needed to protect the data in Padu.
When the government handles data of this size, the risk in terms of data intrusion and security is a significant concern. The development of Padu has taken into account all the aspects of system security risks and classified information breaches,” he said.
In a report by Channel News Asia, the minister added that measures adopted include establishing comprehensive standard operating procedures as well as strategic cooperation between groups – namely the National Cyber Security Agency (NACSA), the Office of the Chief Government Security Officer (CGSO), CyberSecurity Malaysia and the Department of Personal Data Protection (PDP).
“The government has also appointed a group of independent experts with expertise in various fields who act as a check and balance in ensuring that Padu’s development includes the latest and best safety features,” added the minister.
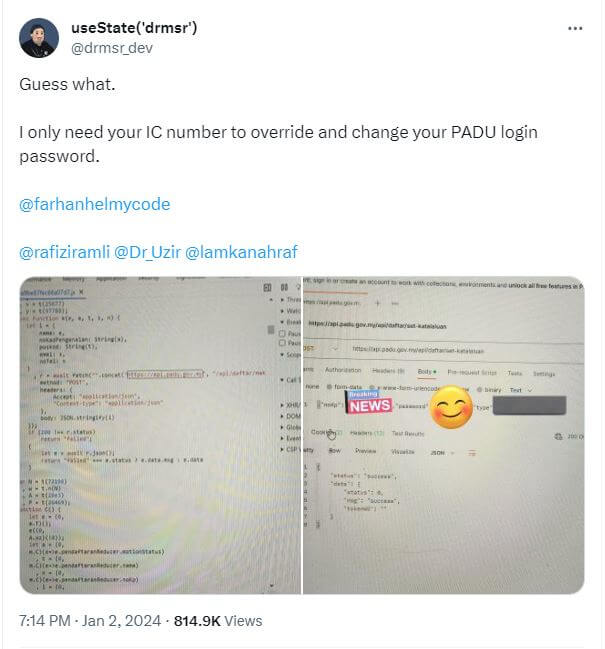
Padu developers were quick to fix a flaw after it was highlighted on X.
How secure is Padu?
Several cybersecurity professionals in Malaysia have raised concerns about the Padu database. Given that the database is also expected to underpin the country’s forthcoming digital ID, many emphasize the need for developers to ensure the absence of backdoors that could be exploited by cybercriminals to compromise the system.
According to a report by The Star, CyberSecurity Malaysia (CSM) chief executive officer Datuk Dr Amiruddin Abdul Wahab said that cyberthreats to the data of millions of Malaysians are real and constantly evolving with technological advancements. Despite this concern, he assured readers that the responsible authorities have undertaken all necessary measures to secure Padu.
“CSM was tasked with conducting a Security Posture Assessment (SPA) as an independent third party. However, the overall requirements and ownership belong to the Malaysian Administrative Modernisation and Management Planning Unit (Mampu) and the Statistics Department. Generally, the cloud is secure for storage, and it is based on the cloud security controls implemented by the cloud service provider,” he added.
Additionally, Dr Amiruddin expressed hope that the government would conduct regular security audits on Padu. He emphasized that, given the ever-evolving nature of threats, the current security system does not guarantee future safety.

Former DAP MP Ong Kian Ming has urged the government to suspend the registration of users for the Central Database Hub, or Padu, until concerns over security issues are resolved.
Five ways the central database hub can be compromised
The Tech Wire Asia team decided to register their details on the system. Initially, the layout and design of the system seemed very amateurish, resembling the work of student developers. The database appeared to predominantly focus on sources of income, which seems redundant since most individuals already declare their taxes to the Inland Revenue Board of Malaysia.
If Padu aims to streamline subsidies to deserving individuals, it may face challenges, particularly because many who need government assistance are in rural areas with limited access to the platform.
The registration process was straightforward. However, the eKYC component, highlighted as complex by several parties, was the most challenging aspect. A former MP even suggested that the government should suspend the registration of accounts until all security concerns on the platform have been addressed.
With that said, here are five ways hackers and cybercriminals could easily compromise the Padu platform.
Identity theft – While some have denied this is a possibility, the reality is that once a cybercriminal has access to an account, they will also have access to all the information that is available. That includes not only personal data but also financial data, including the source of any recorded income.
Such information would fetch a hefty price on the dark web. Hackers could also use the information to set up accounts on other sites, causing havoc to victims. For example, a hacker could use the information for financial identity theft, in which the malicious actor uses financial details to apply for and obtain credit, loans, goods, and services.
Brute force attacks – A brute force attack uses trial-and-error to guess login information and encryption keys, or find a hidden web page. Hackers work through all possible combinations hoping to guess correctly.
For Padu, once a user has verified their account, there is no multi-factor authentication needed to log in to their accounts. All that is needed is the identity card number and password – which can be easily compromised. In fact, the Economy Ministry has thanked a member of the public who found a loophole within its system that allowed third parties to use identity card numbers to override passwords in Padu.
DDoS attacks – A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt online services or sites by overwhelming its target with unusually high volumes of data traffic. Hackers can easily launch DDoS attacks on the platform to disrupt its services. For example, in Singapore last year, a DDoS attack disrupted the country’s public healthcare institution website for hours, leaving many unavailable to log in and such.
Application vulnerabilities – No matter how secure it is, or how big a budget an organization has, all software has some flaws or bugs that can be exploited by cybercriminals. The developers of Padu need to constantly update their software to the latest version. They should also avoid downloading or installing software from untrusted sources or clicking on suspicious links or attachments.
Currently, Padu says that the responsibility for data security lies with the source of the data – meaning each government agency from which the data is coming. But this mentality needs to change as data security needs to be a collective responsibility.
Data breaches – Everyone knows the weaknesses in Malaysia’s cybersecurity laws and the number of data leaks, breaches and such that have occurred in government agencies. As a matter of fact, the current PDPA laws in Malaysia exclude government agencies. Hence, if a data breach was to occur on the database, who would be responsible for it?
The bottom line is that the central database hub is definitely a system that could be a game-changer for Malaysia. But if the concerns raised are not addressed properly, the platform could end up causing more harm to the public instead of benefiting them. With the country’s digital ID plans on the horizon, improving the security features in Padu should be a prerogative that must not be taken lightly.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network




