
Unmasking the human factor in managing cybersecurity risks. (Generated with AI).
Managing cybersecurity risks caused by employees can be as harmful as hacking in APAC
- Managing cybersecurity risks is vital as employee breaches can be as impactful as hacking.
- Kaspersky’s study highlights the significant role of internal employee actions in cybersecurity threats and hacking.
- APAC’s high rate of employee security policy breaches presents a significant cybersecurity concern.
Over the last two years, many companies have faced at least one cyberattack, with some experiencing up to six. Responses to these breaches vary: while some organizations focus on implementing new automated security tools, others prioritize expanding their IT staff, managing cybersecurity risks internally, or outsourcing security solutions.
Training and education play a role in cybersecurity strategies, but perhaps not as significantly as they should, given that most cyber-incidents in recent years are attributed to human mistakes. A study by Kaspersky highlighted that employee breaches of security policies are just as dangerous as external hacking threats.
The role of employee conduct in managing cybersecurity risks
In the Asia Pacific (APAC) region, 33% of business cyber-issues were due to deliberate security protocol breaches by employees. This finding is nearly as impactful as the 40% of breaches caused by hacking. These figures slightly exceed the global averages of 26% for employee violations and 30% for hacking incidents.
The general view is that human error is critical in business cyber-incidents, but the reality is more nuanced. The overall state of a company’s cybersecurity involves several complex factors beyond just human error.
In January 2020, Marriott International faced a significant cybersecurity breach. Hackers exploited vulnerabilities in a third-party application used by Marriott to deliver guest services, gaining unauthorized access to the personal data of 5.2 million guests. This compromised data encompassed a range of sensitive information, including passport details, contact information, gender, birth dates, loyalty program particulars, and individual preferences.
The breach was orchestrated by hijacking login credentials belonging to two Marriott employees, allowing the attackers to infiltrate the hotel’s third-party service system. Despite the infiltration, Marriott’s security measures failed to detect the abnormal activities associated with these employee accounts for approximately two months. The breach was eventually identified and contained by Marriott’s security team towards the end of February 2020.
This incident at Marriott International highlights the multifaceted nature of cybersecurity threats, including those caused by internal vulnerabilities and third-party applications. It serves as a potent reminder of the need for comprehensive security measures encompassing technology and human factors.
Enhancing security protocols in APAC
Kaspersky’s research involved surveying IT security professionals from small and medium enterprises (SMEs) and larger organizations worldwide. The survey, which included 234 respondents from the Asia Pacific region, aimed to understand the influence of various internal and external individuals on a company’s cybersecurity. The study found that policy breaches by regional employees are a significant issue, alongside genuine mistakes.
In APAC, intentional cybersecurity rule breaches occurred among IT and non-IT staff. Violations by senior IT security officers accounted for 16% of cyber incidents, surpassing the global average. Breaches by other IT and non-IT staff resulted in 15% and 12% of incidents, respectively.
The study also identified common problematic employee behaviors, such as using weak passwords or failing to update them, leading to 35% of cyber-incidents in the past two years. This is higher than the global rate of 25%. Additionally, 32% of breaches were due to employees visiting insecure websites, and 25% occurred because of delayed software or application updates.
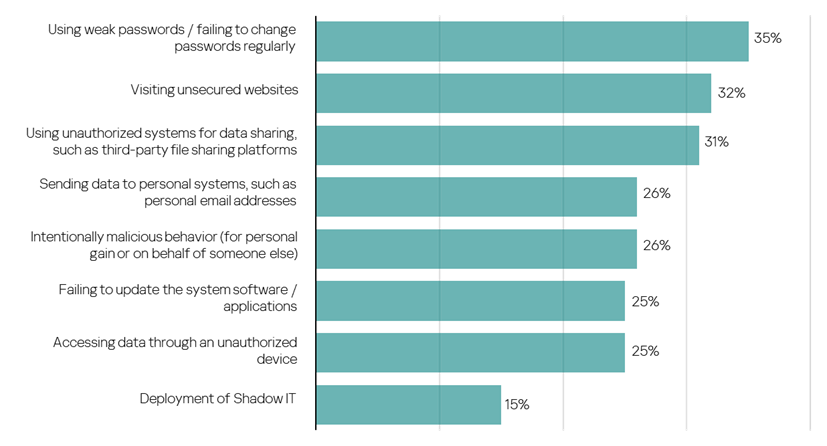
Results of Kaspersky study for the Asia Pacific (APAC) region. (Source – Kaspersky).
According to Adrian Hia, managing director for Asia Pacific at Kaspersky, the continual breaches of basic security policies by employees, despite high-profile cyberattacks, are concerning. “With this latest study showing APAC’s numbers always higher than the global average, a multi-departmental approach to building a strong enterprise cybersecurity culture is urgently needed to address this human factor gap that is being exploited by cybercriminals,” Hia added.
Deliberate security policy violations also include using unauthorized services or devices. Around 31% of companies experienced breaches due to unapproved data-sharing methods, and many employees used unauthorized devices or personal emails for work purposes, contributing to security incidents.
Building a culture of digital safety
It’s concerning that, in addition to previously mentioned irresponsible behaviors, a significant portion (26%) of cyber-misdeeds in the APAC region was carried out by employees seeking personal benefit. Particularly noteworthy is the prevalence of deliberate breaches of information security policies in the financial sector, where 18% of respondents acknowledged such incidents.
Human errors playing a role in a data breach. True or false? (Source – X).
Cybersecurity risks are not only external; they also include various internal elements within an organization. Employees across all departments, be it non-IT or IT security roles, can impact cybersecurity, sometimes inadvertently and other times deliberately. Consequently, it’s crucial to adopt strategies that prevent breaches of information security policies, endorsing a holistic approach to cybersecurity.
Alexey Vovk, Kaspersky’s head of information security, emphasizes the gravity of these findings. He advocates the establishment of a strong cybersecurity culture within organizations from the outset. This involves formulating and enforcing stringent security policies and enhancing employee awareness about cybersecurity. Such initiatives ensure that employees are more conscientious and fully comprehend the implications of any security policy infringements.
READ MORE
- Data Strategies That Dictate Legacy Overhaul Methods for Established Banks
- Securing Data: A Guide to Navigating Australian Privacy Regulations
- Ethical Threads: Transforming Fashion with Trust and Transparency
- Top 5 Drivers Shaping IT Budgets This Financial Year
- Beyond Connectivity: How Wireless Site Surveys Enhance Tomorrow’s Business Network




